Identity Access Management – IAM
- Controlling Users (end users), Groups (collection of users with same permissions, Roles (Can be assigned to resources), Policy (a document that define one or more permissions. Can be assigned to user, group or roles)
- Identity Federation (Active Directory, Facebook, LinkedIn)
- Multi-Factor authentication
- Temporary access for users, devices or services
- Password Rotation policy
- Supports PCI DSS Compliance
Hands On IAM
- Login to aws.amazon.com . Create account if necessary. For this course, free is ok.
- From Security tab, select IAM under Security, Identity and Compliance heading.
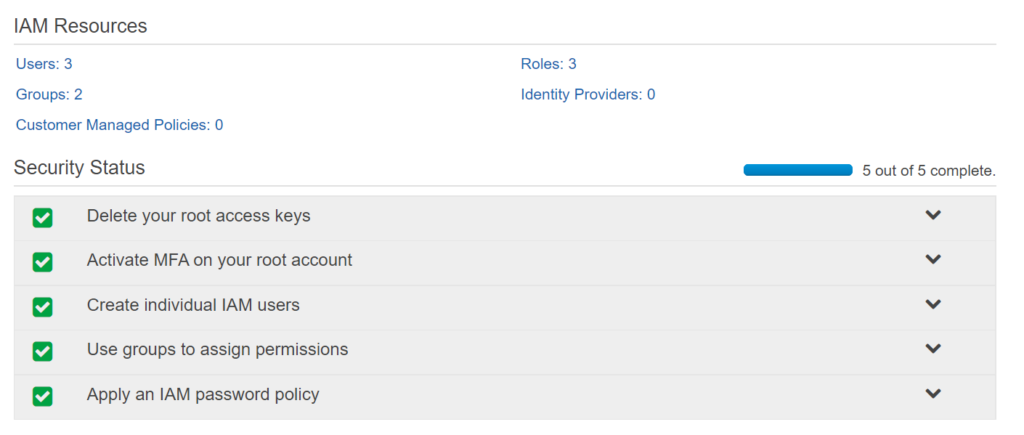
- On IAM dashboard set all the Security Status to Green, one by one.
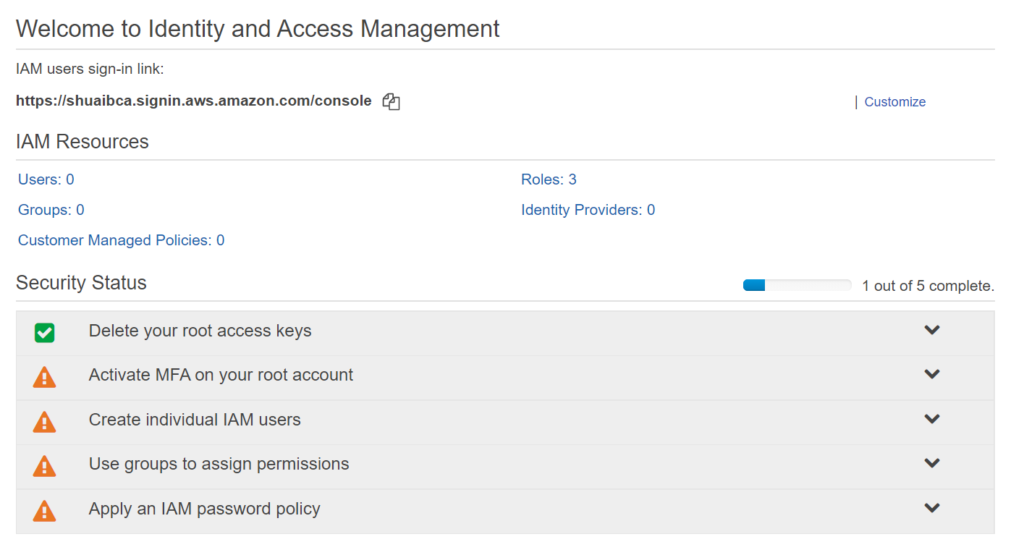
Step 1: Delete your Root Access Keys
Delete if they exist.
Step 2: Activate Multi factor authentication MFA.
Click on Manage MFA and then click on Activate MFA
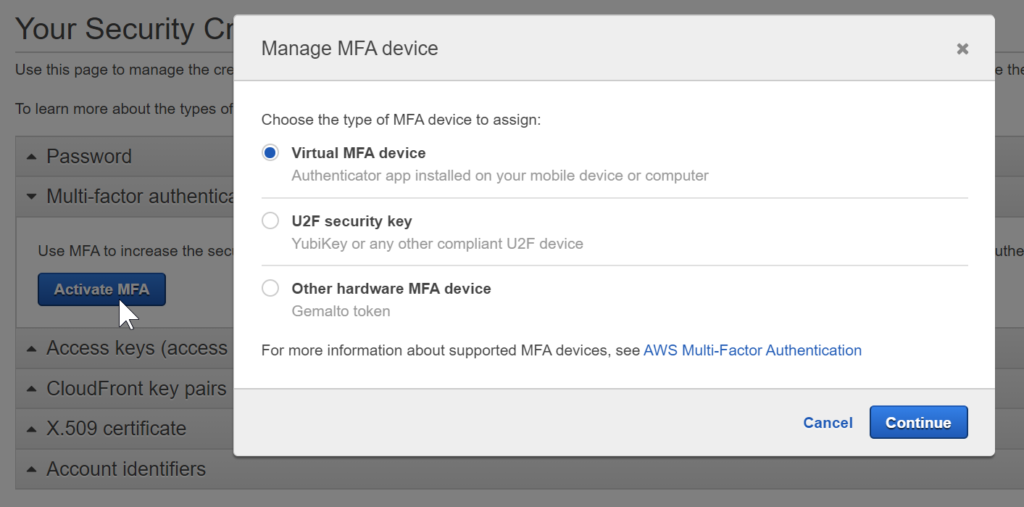
- Select Virtual MFA device
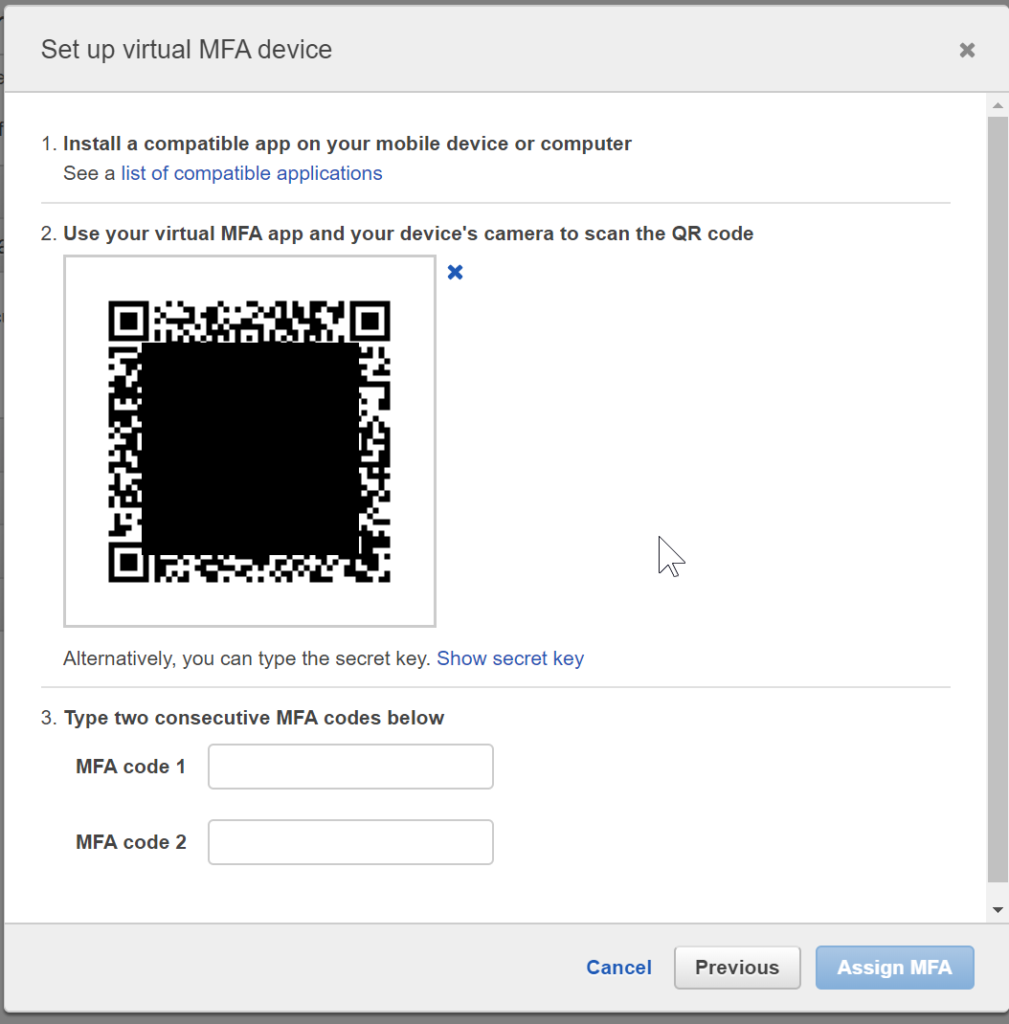
- On your android or iphone, install Google Authenticator . For full list of MFA clients, review the list.
- Scan QR Code and follow the instructions to link your device with the account.
Step 3: Create IAM Users
- Click on Users link in left menu.
- Click on Add User
- Enter username admin
- For this user select both programmatic access and AWS Management Console access.
- Select AutoGenerated Password or Custom Password
- Select Require Password Reset
- Don’t add to a group at this step
- Add no Tags.
- Review User and the hit Create user

- Once the user has been created, you can download the access key.
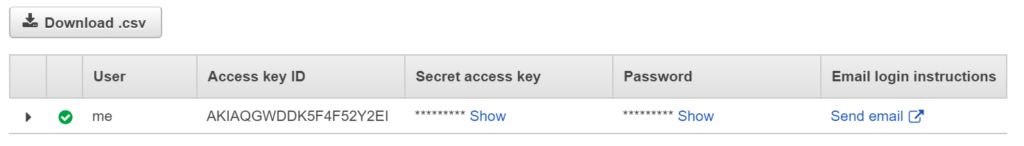
- Keys are needed on Command Line Interface.
- Only time we can see Secret Access Key is when we create the user. We can download it as .CSV
Setp 4: Use Groups to Assign Permissions
- Click Groups in left menu
- Add Group
- Group Name SysAdmin
- For Policies select AdministratorAccess
- Review JSON code of a plicy. it looks like the following:
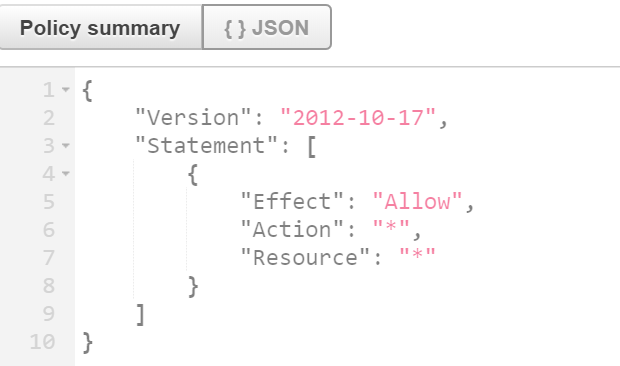
Create another user and another group
- Create another user John
- Create a new group HR
- For this group assign policy AmazonS3ReadOnlyAccess . JSON for this policy looks like following:

- Assign John to HR group.
- Adding permission to user John directly: Select the user, go to Permissions, click on Attach existing policies.
- In Policies, search for AmazonGlacierFullAccess (This user will be responsible for achiving).
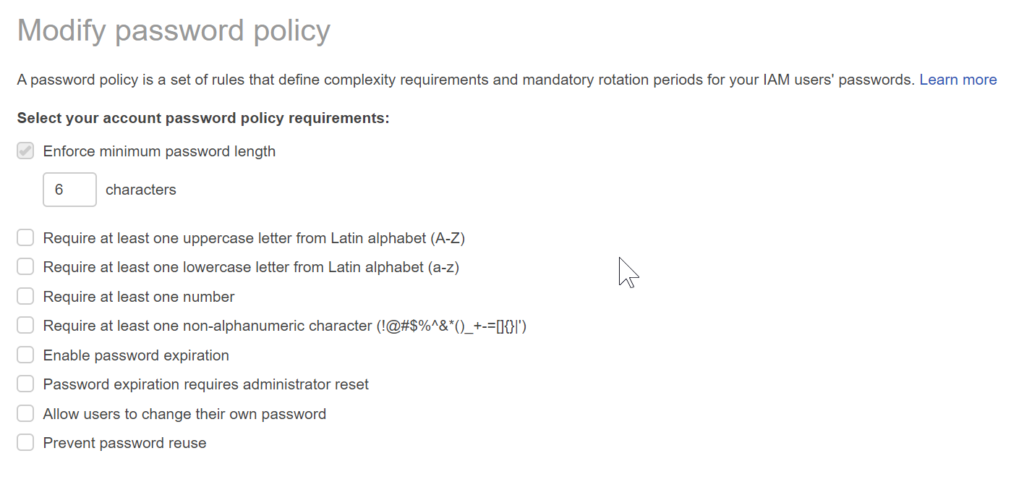
Step 5: Apply an IAM password policy
Click on Apply an IAM Password Policy and then click on Manage Password Policy . Select the policy items.
Create a Role
- From left menu select Roles
- Select Create Role
- Select AWS Service
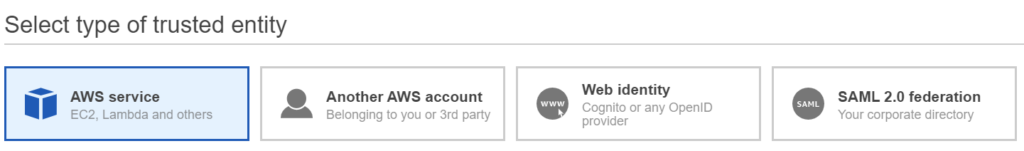
- Select EC2 click on Next
- From Policies select AmazonS3FullAccess
- Next. Finish
What is a Role:
IAM roles are a secure way to grant permissions to entities that you trust. Examples of entities include the following:
- IAM user in another account
- Application code running on an EC2 instance that needs to perform actions on AWS resources
- An AWS service that needs to act on resources in your account to provide its features
- Users from a corporate directory who use identity federation with SAML
IAM roles issue keys that are valid for short durations, making them a more secure way to grant access.
By now, we are done with creating Users, Roles and making all Security statuses green:
Important Notes on IAM
- IAM is Universal – does not apply to reigons.
- root account is the account created when first AWS account is setup. Its complete ADMIN access.
- New Users have NO PERMISSIONS when first created.
- New Users are assigned Access Key and Secret Access Key only when they are first created. Key can be downloaded. It cannot be downloaded later.
- Username/Password are used to login to AWS Managment Console
- Access Key / Secret Key are used to access AWS via APIs and Command Line.
- Always setup Multi Factor Authentication on root account
- You can have your own Password rotation policies

